There are several ways of logging into a server over SSH. Methods include password login, key-based login and two-factor authentication.
Two-factor authentication is a much better type of protection. In the event that your computer gets compromised, the attacker would still need an access code to login.
In this tutorial, you will learn how to set up two-factor authentication on Debian 9 using Google Authenticator and SSH.
Prerequisites
- A Debian 9 server (or newer).
- A non-root user with sudo access.
- A smart phone (Android or iOS) with the Google Authenticator App installed. You can also use Authy or any other app supporting Time-based One-Time Password (TOTP) logins.
!! BEFORE STARTING THE FOLLOWING MODIFICATIONS, I STRONGLY RECOMMEND TO OPEN A SECOND SSH CONNECTION TO YOU SERVER. IF SOMETHING GOES WRONG, YOU WILL STILL HAVE AN ACTIVE CONNECTION TO YOUR SERVER TO UNDO OR REVIEW THE CHANGES YOU MADE !!
Step 1: Installing the Google Authenticator Library
We need to install the Google Authenticator Library module available for Debian, which will allow the server to read and validate codes.
sudo apt update
sudo apt install libpam-google-authenticator -y
Step 2: Configure Google Authenticator for each user
Configure the module.
google-authenticator
Once you run the command, you will be asked certain questions. The first question will be Do you want authentication tokens to be time-based (y/n)
Press Y and you will get a QR code, secret key, verification code, and emergency backup codes.
Take out your phone and open the Google Authenticator app. You can either scan the QR code or add the secret key to add a new entry. Once you have done that, note the backup codes and keep them safe somewhere. In case your phone gets misplaced or damaged, you can use those codes to login. These codes can be used for authentication if you lose your device, but be aware that each code is only valid once.
For the remaining questions, press Y when asked to update the .google_authenticator file, Y for disallowing multiple uses of the same token, N for increasing the time-window and Y to enable rate-limiting.
You will have to repeat this step for all of the users on your machine, otherwise they won’t be able to login once you are through with this tutorial.
Step 3: Configure SSH to use Google Authenticator
Now that all users on your machine have set up their Google authenticator app, its time to configure the SSH to use this authentication method over the current one.
Enter the following command to edit the sshd file.
sudo nano /etc/pam.d/sshd
Find the line @include common-auth and comment it out, like what is shown below.
# Standard Un*x authentication.
#@include common-auth
Add the following line to the bottom of this file.
auth required pam_unix.so no_warn try_first_pass
auth required pam_google_authenticator.so
The first line tells PAM to authenticate with a normal Unix user password before other methods. The second line specifies an additional method of authentication, which in this case, is the TOTP software we installed earlier.
Press CTRL + X to save and exit.
Next, enter the following command to edit the sshd_config file.
sudo nano /etc/ssh/sshd_config
Find the term ChallengeResponseAuthentication and set its value to yes. Also find the term PasswordAuthentication, uncomment it, and change its value to yes. Also check UsePAM setting. This must be uncommented and set to yes
ChallengeResponseAuthentication yes
PasswordAuthentication yes
UsePAM yes
Save and close the file by pressing CTRL + X. Now that we have configured the SSH server to use the Google Authenticator, its time to restart it.
sudo service ssh restart
You should now be able to log in using your SSH key as the first method of authentication and your verification code as the second. To test your configuration, log out and try to log in again via SSH.
You will se the following messages:
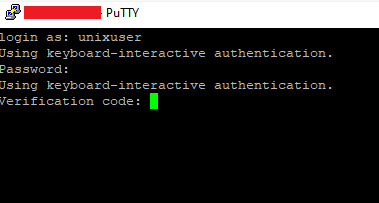
The combination of password and TOTP code must be valid, or else, login is not possible
